15 AWS Security Services for Protection, Compliance & Automation
Security is a non-negotiable aspect of any IT infrastructure, serving as the foundation for trust and reliability in today’s digital landscape. As one of the six pillars of the AWS Well-Architected Framework, security is a foundational aspect; not an afterthought.
Operating under a shared responsibility model, AWS ensures a secure infrastructure, offering a suite of robust tools and services. However, it’s our responsibility to configure, manage, and integrate these tools to meet specific security and compliance needs effectively.
In this article we will explore key AWS services that empower us to protect our applications, ensure compliance, and how can we use these services to automate security tasks, enabling us to build a secure and resilient workloads on the AWS cloud.
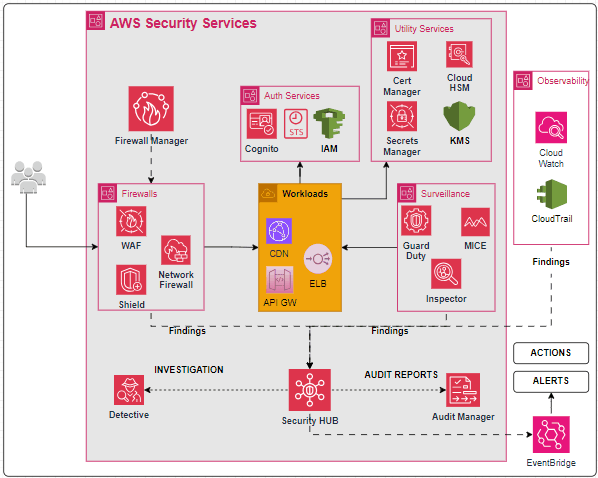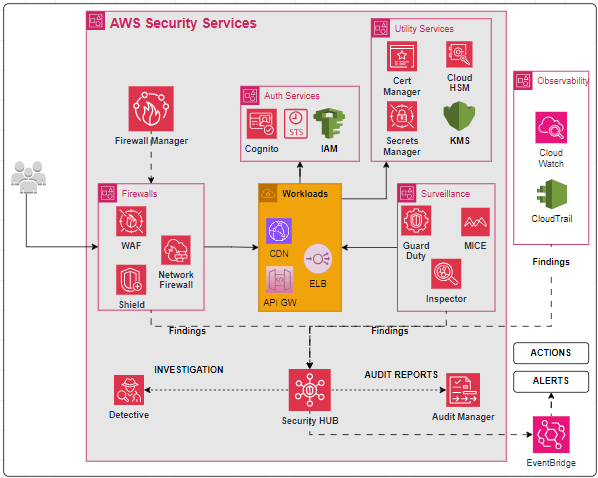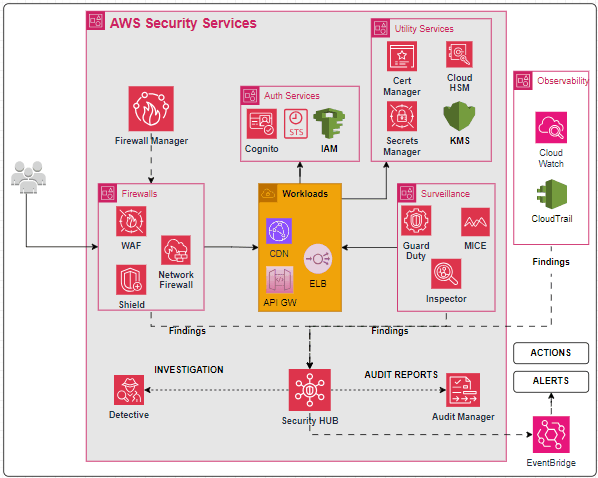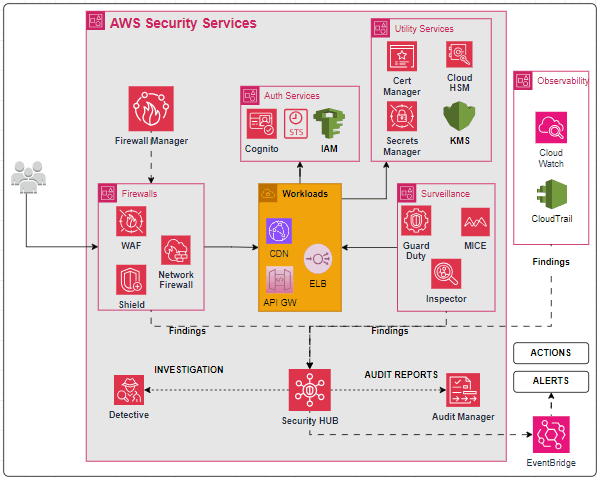
Protect , Comply and Automate Security in AWS
AWS offers a range of powerful tools to keep your applications, data, and traffic secure while meeting compliance needs. The diagram above summarizes the key service related to security and shows how can they be integrated together for securing and automating security needs. In order to create a mind map of how all of these services work together, we have segregated them into the following key categories :
1. Firewalls
2. Auth Services (or Identity Management)
3. Utility Services
4. Continuous Monitoring(or Surveillance)
5. Reporting & Automation
1. Firewalls
Firewalls provide the first layer of Security by keep a check on the incoming traffics. We have WAF(Web Application Firewall), Network Firewall, AWS Shield to protect us from malicious traffic.
WAF works inspects Http/Https (layer 7) requests and protects web applications from attacks like SQL injection, cross-site scripting (XSS), and other OWASP Top 10 vulnerabilities.
Network firewall, on the other hand, examines packets across various protocols working at layer 3 and 4. Secures the entire network by filtering traffic based on IP addresses, ports, and protocols.
AWS Shield is meant to handle DDoS attacks.
AWS Firewall Manager enable us to centrally control and standardize the firewall rules across all our accounts.
2. Auth Services (or Identity Management)
The legitimate traffics entering the network and for all internal/external communications the user and their access permissions needs to be validated.
The services like Cognito, IAM, STS(Secure Token Service) help us implement such authentication and authorization needs. These services support various auth mechanisms like OAuth 2.0, JWT , SSO and Federated Authentication and allow us to securely communicate with various internal and external systems.
3.Utility Services
AWS Secrets Manager is a service to store sensitive data like DB Credentials, API Keys, allowing applications to access them Securely when needed.
AWS Key Management Service (KMS) or CloudHSM centralize the management of encryption keys for encrypting sensitive data at rest or in transit and, also, for digitally signing documents.
AWS Certificate Manager (ACM) makes it easy for you to centrally manage your SSL/TLS certificates and use it from the AWS Management Console, AWS CLI, or ACM APIs.
4. Continuous Monitoring(or Surveillance)
Continuous monitoring of suspicious activities and vulnerabilities is as important as settings up of a strong security framework.
We can use Amazon Mice , a ML based pattern matching security service, for discovering a growing list of sensitive data types, including personally identifiable information (PII) such as Social Security Number, credit card numbers lying unencrypted in our stored data.
Amazon GuardDuty, a threat detection service, enables us to identify unusual API activity in AWS services, detect malicious files and respond to potential security breaches.
Amazon Inspector is a vulnerability management service that continually scans AWS workloads for software vulnerabilities and unintended network exposure.
5. Reporting & Automation
To stay on top of security, AWS Security Hub acts as our central dashboard, collecting and analyzing security and compliance events from across our accounts.
Finding from various security services like AWS GuardDuty, Inspector, Maice, Firewalls, CloudWatch and partner service can be feed into the Security Hub for monitoring and threat detection.
Security Hub can feed its input into AWS Audit Manager for real-time audit reports.
Amazon Detective automates the analysis, investigation, and identification of the root cause of potential security issues or suspicious activities using the findings received from various sources.
Security Hub also streamlines security compliance and incident response processes using integration with AWS EventBridge and other services for alerts and remedial actions.
Conclusion
Amazon provides a wide range of security services to address different aspects of security , security compliance and automation. We can always use other third party security tools wherever we need so. Easy integration options, real-time dashboards , event driven integration for alerting and remedial actions enables us to build highly flexible and robust security systems around our workloads.